Last updated: June 2025
What is Commit Signing?
In Git, you may commit using any name and email address. However, Git supports signing commits and annotated tags using a GPG or SSH key pair.
By signing a commit, others with your public key can verify that the commit was created by you. Public keys can also be uploaded to remote hosting services like GitHub so commits appear as verified.
Commit Signing with GPG
Requirements
Before signing commits, install and configure GPG.
Note: Close GitKraken Desktop before installing GPG.
- Windows: Use Gpg4win and follow the installer.
- Mac: Use Homebrew:
brew install gpg - Linux: Use your package manager:
- Debian/Ubuntu:
apt install gnupg - Fedora:
dnf install gnupg2 - CentOS/RHEL:
yum install gnupg2
- Debian/Ubuntu:
More downloads at gnupg.org.
To verify installation:
gpg --version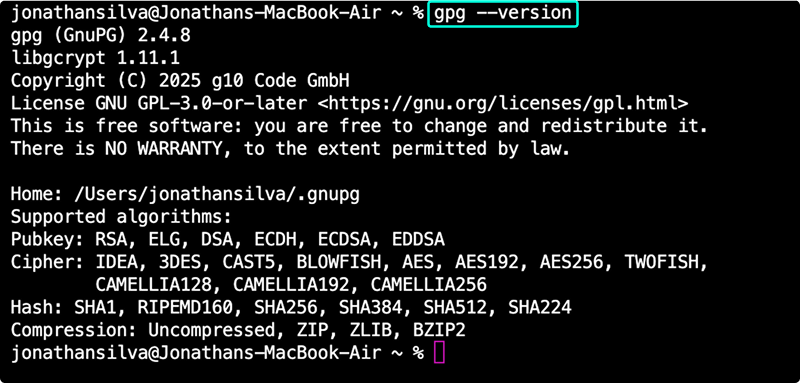
Note: Use gpg2 if gpg isn’t aliased. Prefix commands accordingly.
Generate a GPG Key in GitKraken
Once GPG is installed:
- Go to Preferences > Commit Signing.
- Click Generate new GPG Key.
- (Optional) Enter a passphrase before generating.
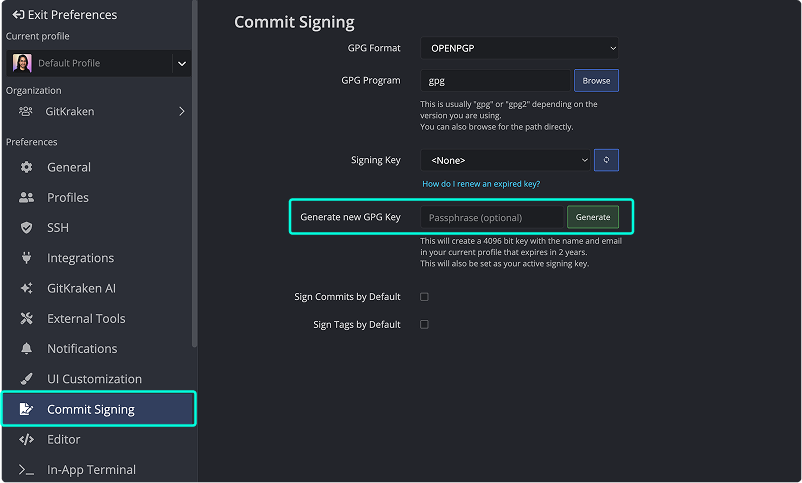
Note: Ensure GPG is configured in GitKraken. See Configure GPG in GitKraken.
Configure GPG in GitKraken
- Navigate to Preferences > Commit Signing.
- Set the Signing Key from the dropdown list. If it’s empty:
- Configure the GPG Program path.
- Restart GitKraken after installing GPG.
- Specify the GPG Program location or use the Browse button if not auto-detected.
which gpg # macOS/Linux where gpg # Windows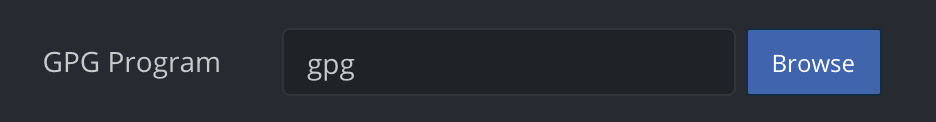
- Enable Sign Commits by Default and/or Sign Tags by Default as needed.
Verifying Signed Commits
Signed commits show an icon next to the SHA in the Commit Panel.
![]()
Hover to view signature details:
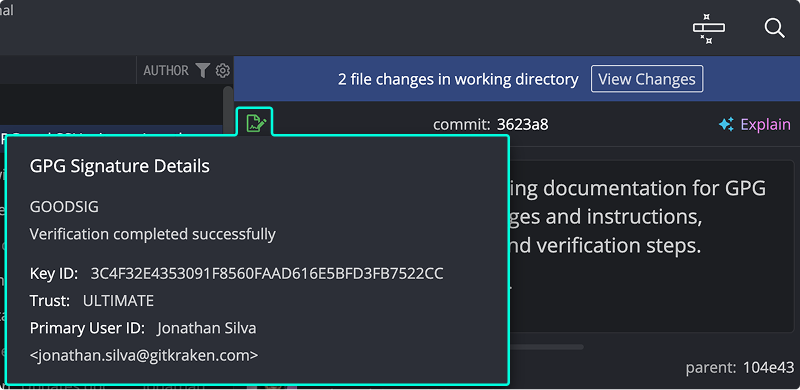
Common GPG signature codes:
GOODSIG: Valid signature.EXPSIG: Signature is expired.EXPKEYSIG: Signed with expired key.REVKEYSIG: Signed with revoked key.BADSIG: Signature not verified.ERRSIG: Unable to check signature (missing key or unsupported algorithm).
Uploading GPG Key to Hosting Service
To display signed commits as verified:
In GitKraken: Preferences > GPG → Copy GPG Public Key.
Editing a GPG Key
To add emails or renew a key:
- List keys:
gpg --list-secret-keys --keyid-format LONG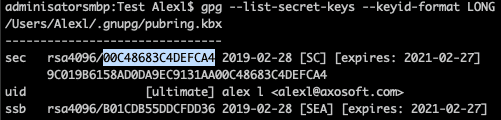
- Edit:
gpg --edit-key YOUR_KEY_ID - Use commands:
adduid: Add emaildeluid: Remove emailtrust: Update trust levelexpire: Change expirationsave: Save and exit
After editing, re-upload the key to your host. See Uploading Your GPG Key to a Remote Hosting Service.
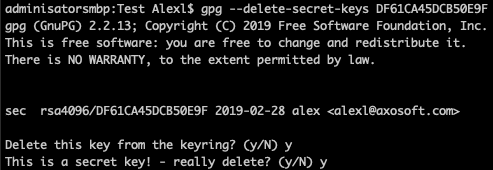
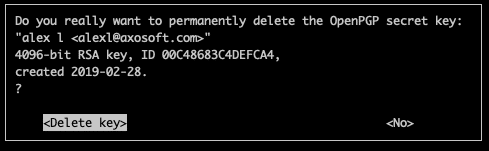
Deleting a GPG Key
To delete:
gpg --delete-secret-keysAppend your key ID or name.
Commit Signing with SSH
SSH signing is available through Git Executable.
Requirements
- macOS/Linux: Git and OpenSSH are usually preinstalled.
git -v ssh -V - Windows: Install Git Bash.
Steps to Enable SSH Signing
-
Create SSH key:
ssh-keygen -t ed25519 -C "[email protected]"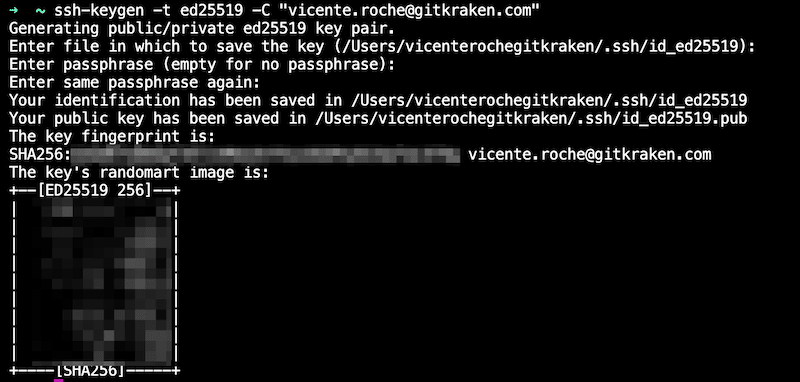
-
Enable Git Executable:
Go to Preferences > Experimental > Git Executable.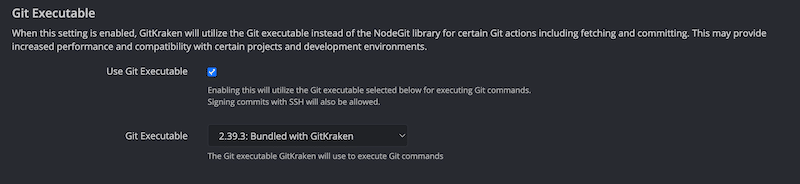
-
Set GPG Format to SSH:
Preferences > Commit Signing > GPG Format → select SSH. -
Select signing key:
On Signing Key, browse to the.pubkey. -
Create allowed_signers file:
touch ~/.ssh/allowed_signers echo "$(git config --get user.email) namespaces="git" $(cat ~/.ssh/YOUR_KEY.pub)" >> ~/.ssh/allowed_signersSelect this file in GitKraken.
-
Enable Signing by Default:
Preferences > Commit Signing → enable Sign Commits and/or Sign Tags. -
Add SSH Key to Host:
- GitHub SSH setup
- GitLab SSH setup
- ⚠️ Bitbucket does not support SSH-signed commit verification.