Last updated: June 2025
GitKraken Desktop supports authentication with most repository hosting services (e.g., TFS, AWS CodeCommit, Google Cloud Source Repositories, and custom services) over HTTPS or SSH.
HTTPS Authentication
This is the default and most common method for interacting with remotes. It requires your Git username and password.
How to clone with HTTPS
-
Copy the HTTPS URL from your hosting service, which typically looks like:
https://example.com/username/myrepository.git -
In GitKraken Desktop, go to File > Clone Repo.
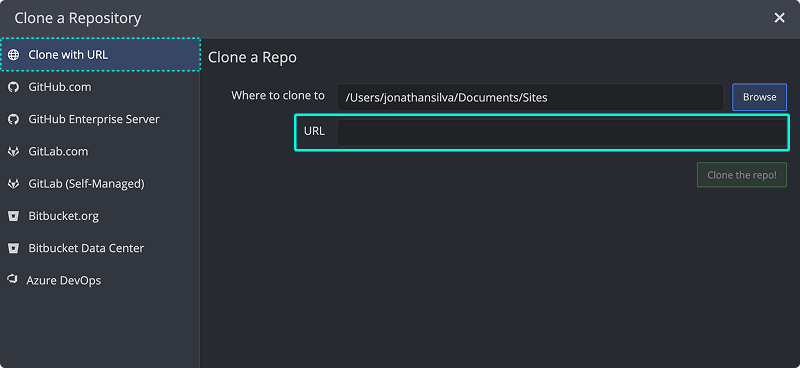
- Paste the URL, click , and open it in GitKraken.
The remote tracking at origin is automatically set using this HTTPS format.
SSH Authentication
Before cloning via SSH, you must first set up your SSH keys in GitKraken Desktop.
Set up SSH keys
- Navigate to Preferences > SSH.
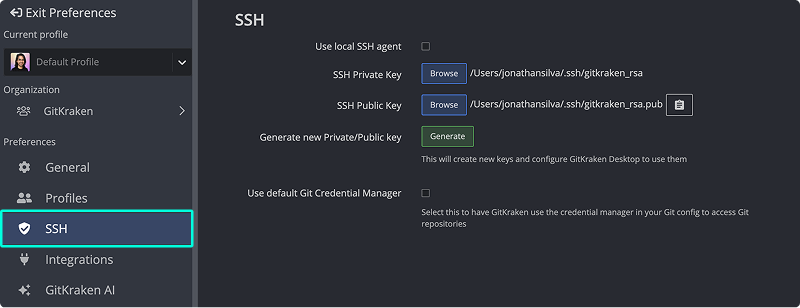
- You can browse to select an existing SSH key pair or generate a new one (recommended).
- Copy the public key to your remote hosting service.
Clone over SSH
- Copy the SSH URL from your hosting service.
- In GitKraken Desktop, go to File Clone.
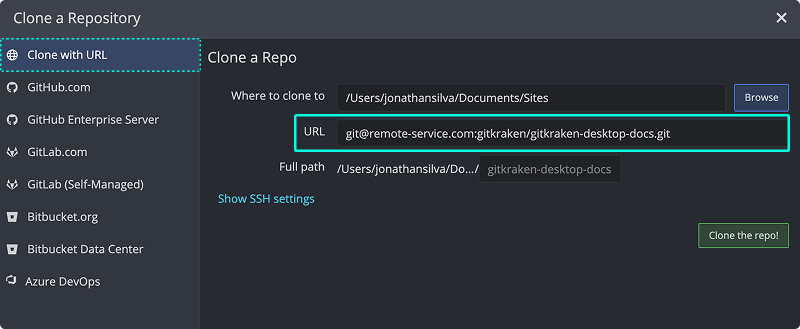
- Paste the SSH URL, click , and open the repo.
Supported SSH formats
ssh://{user}@{host}/{repo}
{user}@{host}:{repo}Where:
{host}is the domain (e.g., example.com){user}is the username (typicallygit){repo}is the path to the repository
Custom SSH ports
Use this format:
ssh://{user}@{host}:{port}/{repo}Use a Local SSH Agent
Using a local agent can simplify SSH management, especially across multiple profiles. From Preferences > SSH, check Use local SSH agent.
Tip: This allows automatic key usage if already loaded in your system’s agent.
Troubleshooting SSH
- Windows: Only Pageant is supported. Download from PuTTY’s site.
- Misconfiguration: Double-check your remote URL format and SSH settings.
- SSH config files: GitKraken Desktop does not support
.ssh/configaliases. Load your key directly or use your OS’s agent.
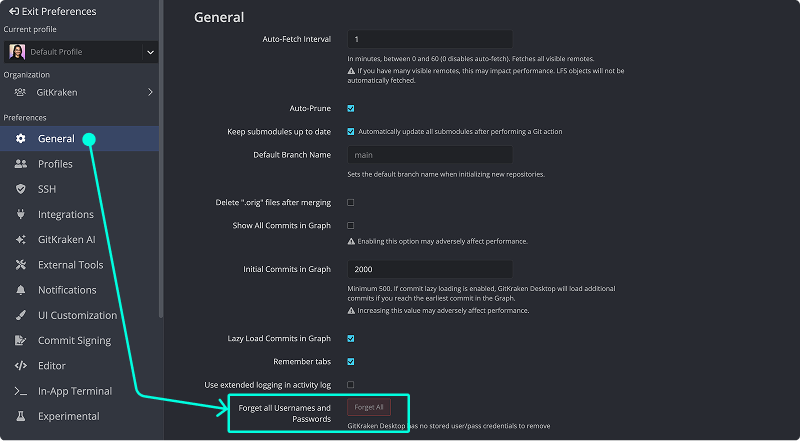
Forget All Credentials
Reset stored usernames and passwords from Preferences > General:
Proxy Configuration
GitKraken Desktop supports proxies for Windows, macOS, and Linux.
Windows
Your system will prompt for proxy credentials when needed.
macOS & Linux
GitKraken Desktop prompts for credentials directly.
On Linux, run with this flag if needed:
--proxy-server=10.200.0.1:8080Google Cloud Source Repositories
Due to formatting, you may need to adjust SSH URLs:
Original:
ssh://[email protected]@source.developers.google.com:2021/p/test-project-12345/r/Test-Repo-1Fixed:
ssh://example%[email protected]:2021/p/test-project-12345/r/Test-Repo-1